
A Sophos Firewall reverseproxy.log analysis script which helps to analyze errors and find thread IDs in the reverseproxy.log file. The thread IDs found are displayed clearly and can be found quickly.
Update 14.10.2025: Script updated to version 1.0
Introduction
Anyone who has ever set up a WAF on the Sophos firewall will know that finding thread IDs is extremely tedious. As I regularly configure WAFs for my customers, the collection of shell commands in my collection was getting longer and longer. A more practical solution was needed. Especially as the output was still difficult to read. From this, the Sophos Firewall reverseproxy.log analysis script offered here was born.
Read on and find out what the script can – or cannot – do.
Have fun analyzing! 😀
Versions
- v0.6
- first release
- v1.0 (10/2025)
- Output better formatted
- Performance improved with perl(grep and sed delayed the output considerably due to buffering)
- Time filter now also filters e.g. ” 9″ and “09”. The entries are sometimes written differently
- Color output of some values
- Help revised
- Error handling improved
- -s and -e option improved
- current time zone is taken into account in the search with -t option
Prerequisites
The following requirements must be met in order to use the script:
- SFOS 19.5.0 to 22.0.x (earlier and later versions may need to be tested)
- Shell access to the firewall
- Basic knowledge of using the shell
What can the script (not) do?
What works?
The script can evaluate the following information and display it in a readable format:
- List thread IDs for current events
- List thread IDs for past events
- List how often threads ID’s were logged in the period 1-2 hours, today and yesterday
- Filter by FQDN and/or source IP
- List all entries with errors or warnings with a blank line between the entries for better readability
- Combinations of the listed functions
- Evaluate your own reverseproxy.log file (from temporary copies or log rotation)
What is not possible?
The script cannot do the following:
- Display errors other than thread IDs, readable reduced to relevant data
- Display errors that cannot be filtered for “Thread IDs” or “Warning” or “Error”.
- Guarantee that the output is always readable. As the variations of the entries are very diverse, it may not be possible to display every line legibly.
- Guarantee that the output of the thread IDs is complete
- Guarantee that there are no other errors that are simply not displayed
Utilization / Parameters
The script can be controlled via several parameters. In general, the script is started as follows if it is located in the /tmp directory.
sh /tmp/waf_analyzer.shWithout parameters, the “/log/reverseproxy.log” file is evaluated and the thread IDs are displayed live. There is no filtering according to, for example, the client IP or the server FQDN.
Parameters
Help
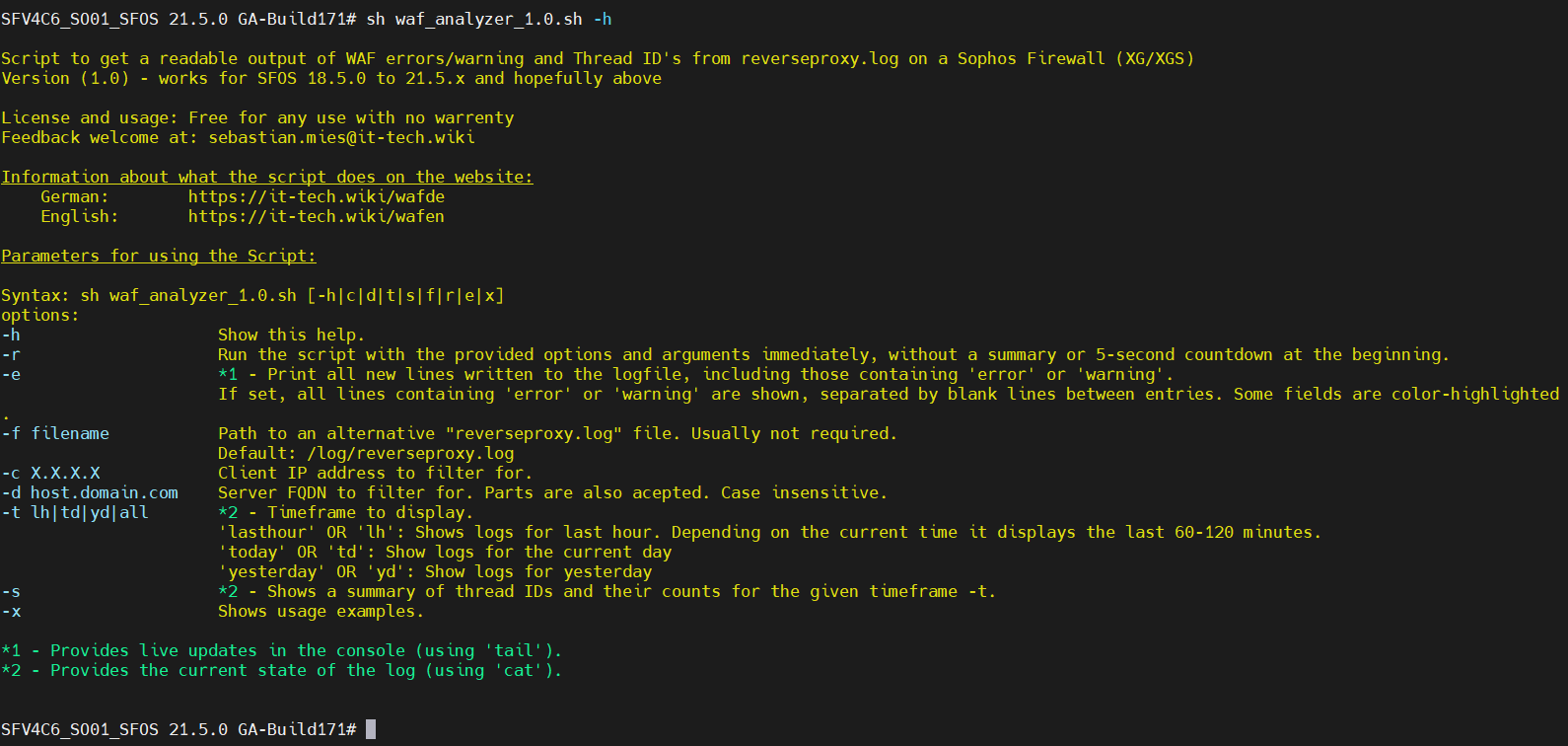
-h
Displays help on the parameters.
-x
Shows examples of use.
Filtering the outputs
-c 169.254.254.254
Filters according to the source IP address and only outputs matching lines.
The parameter is optional.
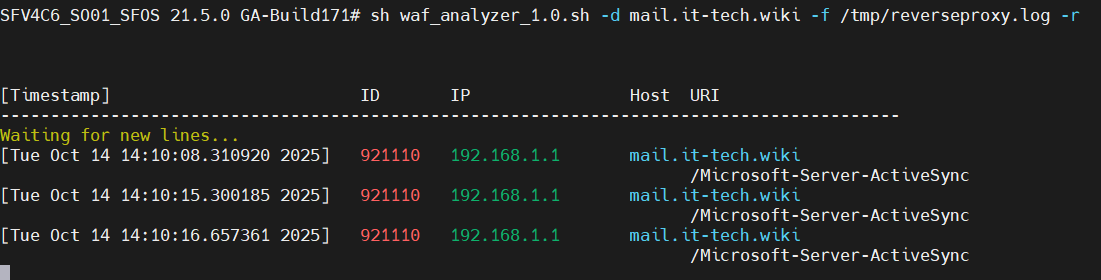
– demo.it-tech.wiki
Filters by FQDN of the WAF and only displays matching lines…
Case-insensitive.
It is also possible to search for parts of the FQDN only. E.G.: -d it-tech
The parameter is optional – but> with “-s” is mandatory.
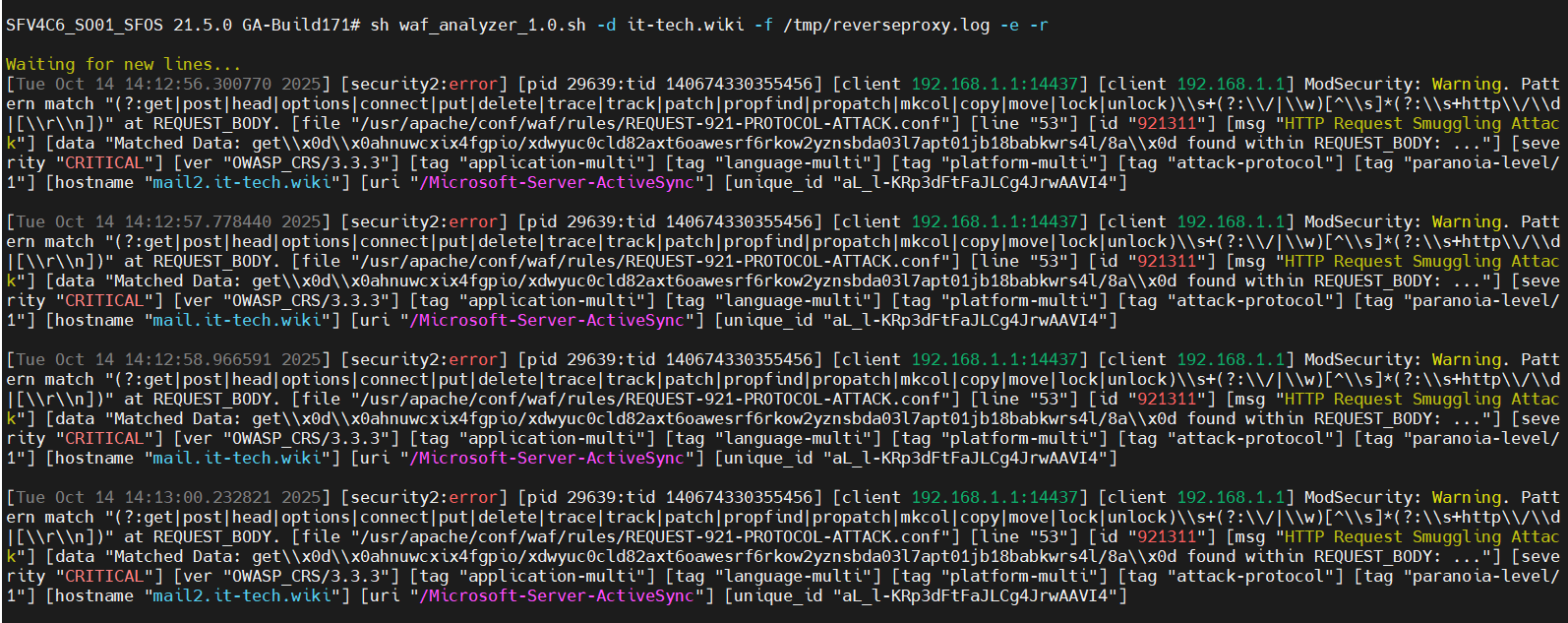
-e
This parameter is not used to evaluate the thread IDs. All lines containing the word “error” or “warning” are output. An empty line is output between the entries for better readability. Some of the individual values are highlighted in color.
Can be combined with -c, -d, -t
The parameter is optional.
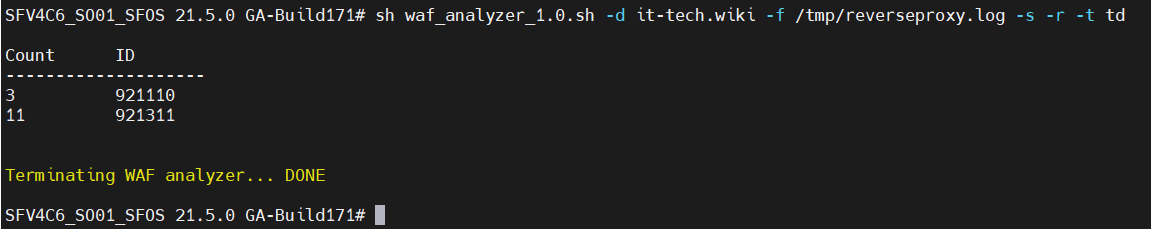
-t option
Displays the data for a past period – no live update.
Possible values are:
– “lh” or “lasthour” = the last 60-120 minutes (depending on the current time)
– “td” or “today” = everything from the current day
– “yd” or “yesterday” = everything from yesterday
– “all” = all data contained in the log file
Can be combined with all parameters.
-s
Displays the frequency of occurrence of thread IDs in the time period of the “-t” parameter. If -t is not set, “lasthour” is selected here.
The “-d domain” parameter is also required.
The parameter is optional.
Miscellaneous
-f /tmp/otherlog.log
If a log file other than “/log/reverseproxy.log” is to be used, this can be set with this parameter.
This parameter is optional.
-r
By default, the script outputs a small summary of the parameters and the command line to be executed before execution and then starts after 5 seconds.
With -r this is skipped and the output starts directly.
The parameter is optional.
Screenshots
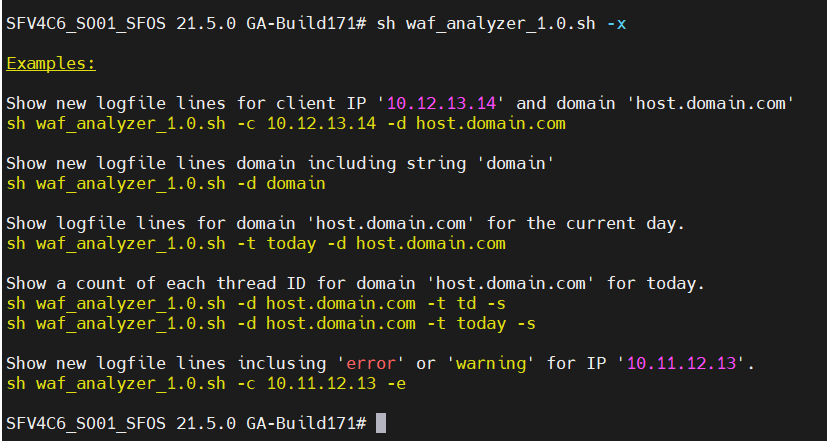
Installation
Direct download
The easiest way is to call the following command on the advanced shell. The “Installer” loads the current version into the /tmp directory and renames any old versions of the script. The script can then be used directly.
curl -L -s -o /tmp/install_waf_analyzer.sh https://it-tech.wiki/wafinstaller && sh /tmp/install_waf_analyzer.sh && rm /tmp/install_waf_analyzer.shManual upload
If you prefer to load the script manually onto the firewall, you can download it here and place it on the firewall yourself.
To upload to the Sophos Firewall, tools such as WinSCP can be used, or the content can be copied directly into the “vi” editor.
Questions
- Does the script make changes to the firewall?
No, the script only reads the lines of the log file and outputs the results directly to the shell. No files in the system are changed.
As the script can be read in plain text, you are welcome to check this. - I have found an error. Where can I report it?
You are welcome to report errors via the contact form or in the comments. - How to remove the script from the system?
Simply delete the file waf_analyzer_X.X.sh in the /tmp directory. For example:rm /tmp/waf_analyzer_0.7.sh - I have a request for the script. Where can I report this?
You are welcome to report errors via the contact form or in the comments.

