
The Internet IPv4 group in the Sophos Firewall contains all possible public IP addresses. But also your own, or others, which sometimes should not be included. This generator for Internet IPv4 group exceptions supports the quick customization of the predefined group and removes the desired IP addresses and networks.
Introduction
In my last projects with Sophos Firewall I always had a problem when using the "Internet IPv4 group". If you use the object in SD-WAN rules, the packets on the firewall are routed to the WAN or to another defined gateway via the corresponding SD-WAN rule. That's fine as far as it goes. However, this is different when using the WAF from internally or DNAT Loopback. In this case, the packets should not go to the Internet, but be processed by the firewall. This is very annoying and can only be found out by analyzing the routing information very precisely in the logs or the conntrack.
The problem can also occur in other constellations where, for example, you do not want to route all public IP addresses in the SD-WAN rule. Of course, you can always make a higher-level SD-WAN rule that routes to a different location or to the firewall itself in individual cases - but it's not always nice.
At some point I no longer found the customization of the objects fun and set about creating this generator. And here is the generator for Internet IPv4 group exceptions!
When exactly does the problem occur?
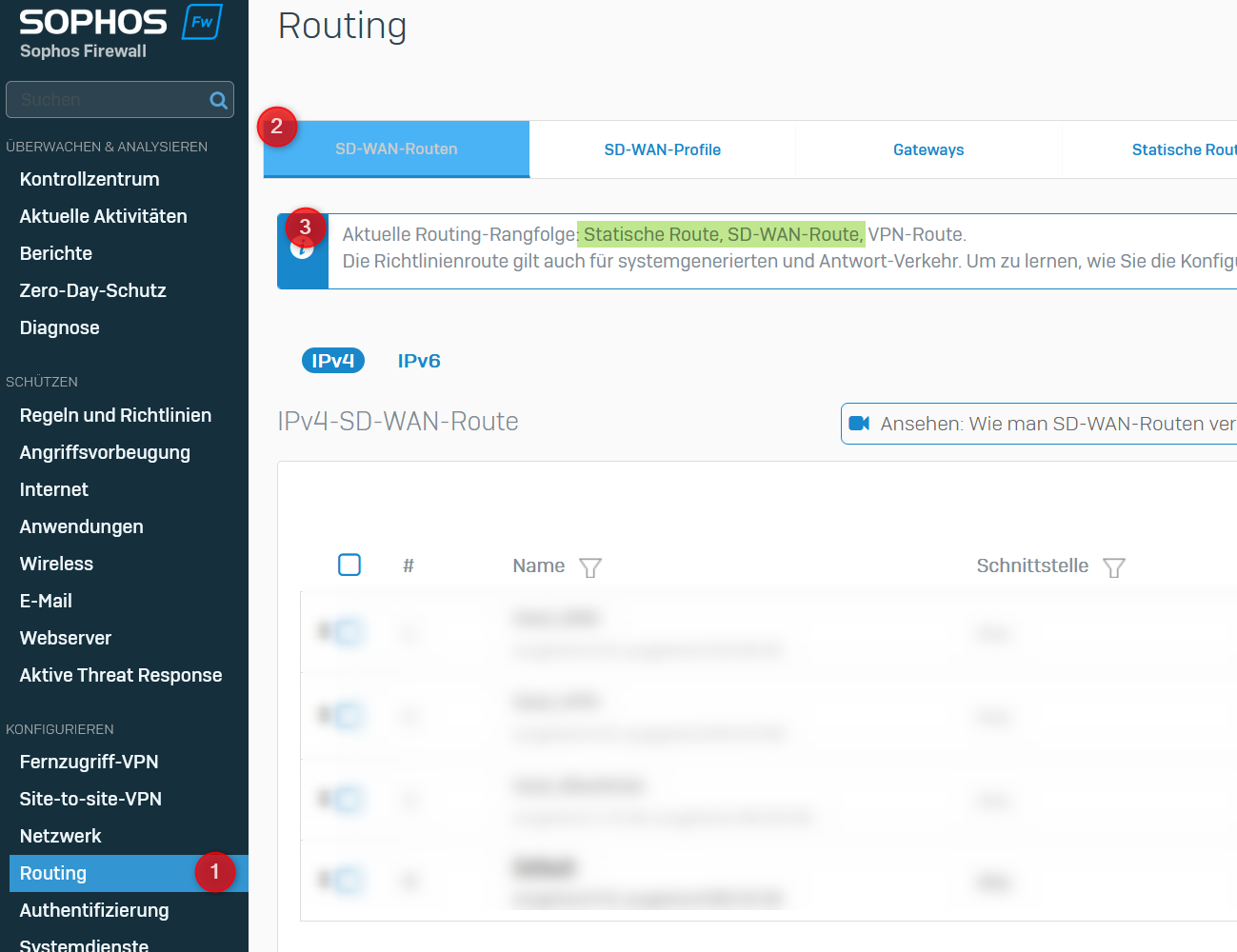
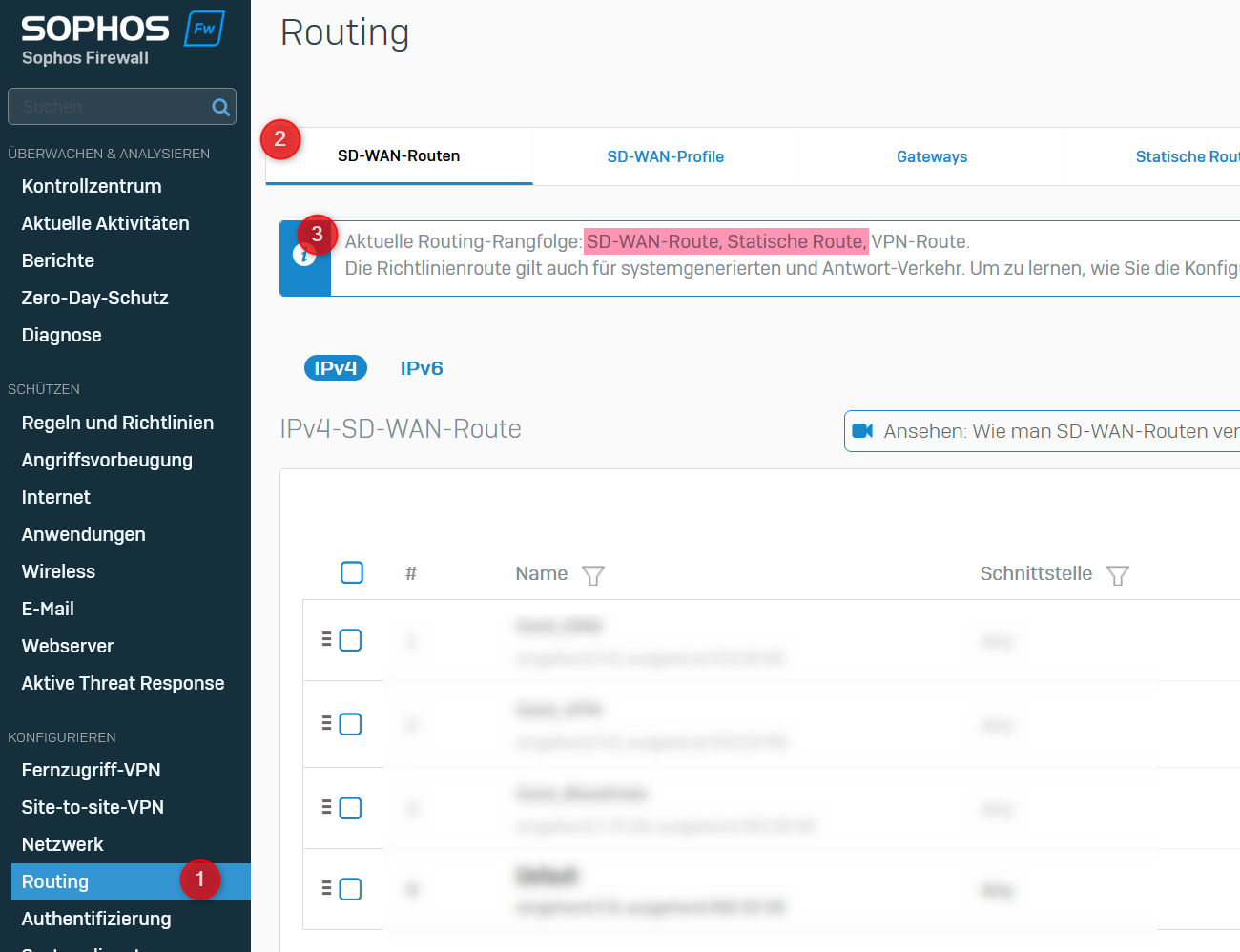
The routing priority must state that "SD-WAN" takes precedence over "static routes". Only then can you run into this problem. If the priority is the other way around, I have not yet been able to observe the problem. It doesn't matter where "VPN" is in the sequence - unless public IPs are used in the VPN tunnel, in which case the issue can also occur if "SD-WAN" comes before "VPN".
How can I change the priority? Here is a guide from Sophos.
You can check them in the WebUI as follows:
What does the generator do?
You can use the generator to exclude individual IP addresses or networks from the "Internet IPv4 group" defined by Sophos. Several IPs or networks can be entered individually one after the other. The generator shows the new IP ranges to be created and which objects are no longer required in the new "Internet IPv4 group" group.
Finally, a configuration file can be created using the"Generate new objects" button, which you can then import onto your firewall. The created configuration file only contains the new IP ranges to be created and creates a new group with old and new objects as members. The original areas and the group remain untouched!
The predefined list from Sophos always serves as the basis. This cannot be adjusted:
"1.0.0.0-9.255.255.255"
"11.0.0.0-126.255.255.255"
"128.0.0.0-169.253.255.255"
"169.255.0.0-172.15.255.255"
"172.32.0.0-191.0.1.255"
"191.1.0.0-191.255.255.255"
"192.0.1.1-192.0.1.255" (NEW in v20.0.1: "192.0.1.0-192.0.1.255")
"192.0.3.0-192.88.98.255"
"192.88.100.0-192.167.255.255"
"192.169.0.0-198.17.255.255"
"198.20.0.0-198.51.99.255"
"198.51.101.0-203.0.112.255"
"203.0.114.0-223.255.255.255" (NEW in v20.0.1: "203.0.114.1-223.255.255.255")
Operating the generator
- Under "Network to exclude", enter an area to be excluded from the list. The entry must always be made in CIDR notation. Even if it is only a single address (e.g. 1.1.1.1/32)
- Due to the subnet mask, network addresses are calculated automatically and the entire network is taken into account in the calculation.
- Further areas can be sent one after the other.
- "Reset" resets all information
- "Generate new objects" creates the configuration file that you can import into the firewall. From this point on, the data (the exclusions created) will be stored on our server for 30 minutes!
The download link is only displayed once. So copy the link if necessary before you close the page.
Generator
Versions
15.05.2024 - SFOS 20.0.1 Area adjustments adopted in blog entry and generator
FAQ
Do you have any further questions? Get in touch with us or write a comment! We will endeavor to reply as soon as possible.



Danke, schönes Tool. Erspart in einigen Fällen doch etwas Arbeit 👍
Danke für das feedback!