
The WAF of the Sophos Firewall has a limit on the file sizes that are allowed through the WAF. This article explains how to adjust the WAF 1MB limit on Sophos Firewall - completely manually, or with the help of a script.
Introduction
Sophos uses the Apache server module "ModSecurity" for its WAF. By default, this module has a limit on the file sizes that can pass through the WAF - this is not a Sophos standard. Unfortunately, there is no way to set this limit directly in the GUI or the shell. To do this, you must adjust the value in the firewall database using the advanced shell.
How does the error manifest itself?
In general, you will notice that files over 1MB will not go through. The error message in the respective web application is not always the same. If you check the log entries in the reverseproxy.log file, you will find such an error here:
[DATE] [security2:error] [....] ModSecurity: Request body no files data length is larger than the configured limit (1048576).. Deny with code (413) [....]Adjusting the limit
Prerequisites
The following requirements must be met for implementation:
- Access to the Shell
- Admin password must be known
- SFOS 19.5.x to 20.0.x must be installed. Other versions will also work. However, these are self-tested.
Information about the limit in advance
Please note that the WAF cannot process infinitely large files. It is still a firewall. It is not intended to replace a fully-fledged WAF.
In my tests, I could set 100-200 MB without any problems. Higher limits are conceivable, but in my opinion do not make sense with the WAF.
Nevertheless: The maximum limit is theoretically due to the integer limitation at 2147483647 ≈ 2147 MB ≈ 2,14 GB.
Also bear in mind that an XGS3300 can handle large limits better than an XGS87!
Manual
The traditional way is the manual way. To do this, proceed as follows:
Find out the database ID of the WAF profile
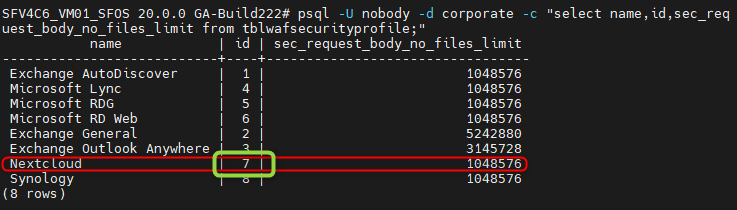
You can use this command to display the WAF profiles in the advanced shell.
psql -U nobody -d corporate -c "select name,id,sec_request_body_no_files_limit from tblwafsecurityprofile;"The command displays the name of the profile, the ID of the profile in the database and the current limit. The ID is required for the next steps.
Adjust database limit
Now replace YYY with the ID of the profile to be customized in the following command.
You also replace XXX with an integer. It stands for the new size in MB.
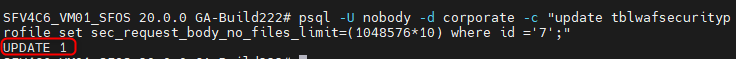
psql -U nobody -d corporate -c "update tblwafsecurityprofile set sec_request_body_no_files_limit=(1048576*XXX) where id ='YYY';"Here is an example in which the limit of profile ID 7 is set to 10MB:
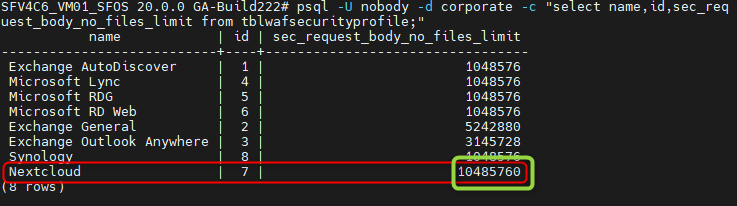
psql -U nobody -d corporate -c "update tblwafsecurityprofile set sec_request_body_no_files_limit=(1048576*10) where id ='7';"Whether the limit has been set successfully is first acknowledged with an "Update 1" in the console. You can check the value with the"List" command from above.
Activate new limit
Finally, the new limit must be activated. To do this, the following command must be sent, which re-reads the WAF configuration once.
opcode waf_reconfig -t json -b '{"Entity": "waf_advanced_config", "Event": "UPDATE"}' -ds nosync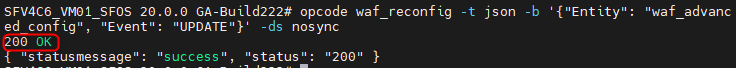
The process is acknowledged with "200 OK". Done, the new limit is active. 😀
Per script
You wanted to adjust the limit more often, are not so confident in using the CLI, or are afraid of making adjustments in the database? No problem! Our ITW script can help here. Just run it and you will be guided through the configuration. You don't need any knowledge of the necessary commands and don't have to worry about typos! 😀
Use of the script
If the script is on your firewall, you can simply start it like this. Please note that the script must always be started with a sh beforehand due to shell regulations.
After calling up the available profiles are listed and you can enter the profile and the limit to be set.
sh /pathtoscript/waf_1mb_change.shYou will then be prompted to confirm and the customization is complete.
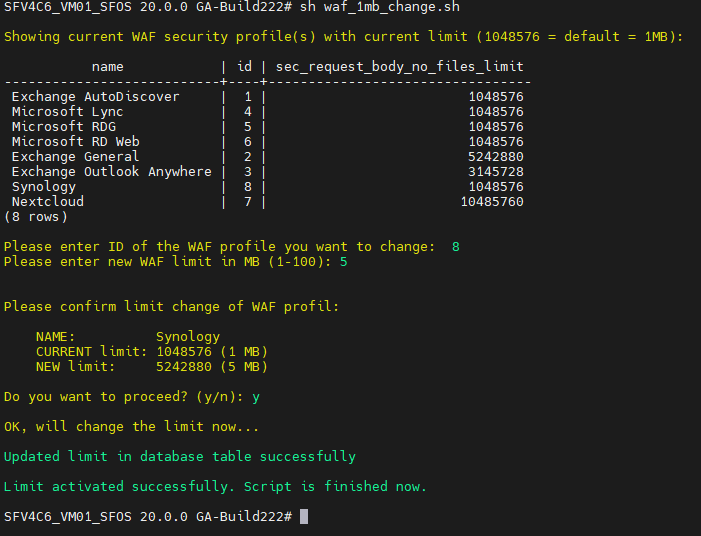
Parameters for the script
- -h
Displays help - -d
Makes a dry run without changing values. At the end, the commands are displayed with which you can also make the adjustment yourself. - -i
Ignores the version (SFOS) of the firewall. For security reasons, untested versions are not accepted and the script terminates. If the script is to run anyway, this parameter must be set - -s searchtext
Limits the list of available profiles if you have a large number. The search is partial and ignores upper/lower case.
Download
Upload yourself
You want to upload the script to the firewall yourself? Then use this download.
Download directly to the firewall
It's even easier with this. You download the script directly in the advanced shell and can start directly.
curl -s -L -o /tmp/waf_1mb_change.sh https://it-tech.wiki/sdc_download/2741/?key=2otn2oerlxhgxsj72esfre99kvvqat && echo -en "\n\nUse \"sh /tmp/waf_1mb_change.sh -h\" to get help for first use\n\n"Questions
- Is the configuration bootable?
A very clear YES 😉 It was like this in the last versions, but it wasn't like this before. Sophos has probably changed something. After a reboot, simply try the limit again to be on the safe side - Is the configuration update-resistant?
Also a very clear YES 😉 It was like this in the last versions, but it wasn't like this before. Sophos has probably changed something. After an update, simply try the limit again to be on the safe side - How secure is the script?
The script has been tested by us as far as possible and should catch all possible input errors. However, the predefined CLI commands mean that nothing can really happen. Nevertheless, we accept no liability for any consequential damage.
If you like, you can also take a look at the source code and check what the script does.
Once again: Test environments are always good! 😉 - Is it possible to reset the configuration?
Yes, simply set the default value again: 1MB = 1048576
Other articles
You are also welcome to take a look at another of our own developments:


Genial, danke! Das erleichtert einiges! 5*
This is excellent info, and the correct way to do it on SFOS. Thanks!
You are welcome! Thanks for the feedback. 🙂