
Introduction
The Sophos Firewall (CLI) console contains some tools, but also some configuration commands that are not available via the WebUI.
Since there is a lot that can be done in the console, I will only show some of the commands here. A full overview can be found in the Sophos Help.
I have selected the following commands because I use them regularly. So a small Sophos Firewall CLI manual with the commands I use most often. I also limit myself to IPv4. Some commands also have alternative parameters or commands for IPv6.
Some of the commands are also available in a different form in the advanced shell. Here, however, you need to have a little more knowledge of the Linux shell. Articles for the advanced shell are linked above.
Console commands
Check hotfix status
Sophos automatically applies critical hotfixes to the firewall. However, the hotfix status cannot be checked in the WebUI. If you want to check your current hotfix status on the console to make sure that the hotfix has already been installed, enter the following here:
system diagnostic show version-infoYou can find the current status under "Hot Fix version".
IP countries review
Do you want to have the country associated with a specific IP address in order to optimize the rules accordingly or evaluate data on the console? The Console offers an option for this:
show country-host ip2country ipaddress 8.8.8.8FQDN TTL
By default, the TTL of FQDNs is also read out with the respective FQDNs via DNS and used to update the entries. However, this behavior can be changed globally to a custom interval.
# Aktuelle Konfiguration anzeigen
# Show current settings
show fqdn-host
# Eigene TTL global setzen
# Set own global TTL
set fqdn-host cache-ttl 3600
# TTL wieder auf TTL der einzelnen FQDN setzen
# Use FQDNs TTL (default)
set fqdn-host cache-ttl dns-reply-ttlReporting / Logs
On Box Reporting
Reporting on the firewall can be globally deactivated or activated. Reporting can only be switched on or off completely. It is not possible to switch individual modules.
# Reporting an/ausschalten
# Switch reporting on/off
set on-box-reports on|off
# Status anzeigen
# show current configuration
show on-box-reportsMax report storage space
The firewall generally cleans up old reports. The maximum amount of memory used by the partition until data is deleted can be set here. By default, the firewall cleans up from 70%.
# Schwellwert einstellen (Standard = 70)
# Set value (default = 70)
set report-disk-usage watermark [default | <50-75>]
# Status anzeigen
# show current configuration
show report-disk-usage watermark# Schwellwert einstellen (Standard = 70)
# Set value (default = 70)
set var-partition-usage watermark [default | <50-75>]
# Status anzeigen
# show current configuration
show var-partition-usage watermarkDelete logs
To quickly free up disk space, for example, or to start from scratch with the logs, there is a command to delete all or old logs.
# Alle Logs unter /log löschen
# Delete all logfile in /log
system diagnostics purge-all-logs
# Alte Logs löschen /log/*.gz
# Delete old logfiles /log/*.gz
system diagnostics purge-old-logsSystem information
The status / utilization of the hardware can be displayed under the console.
# CPU Informationen
# CPU information
system diagnostics show cpu
# Disk Speicherverwendung
# Disk usage
system diagnostics show disk
# RAM Auslastung
# RAM usage
system diagnostics show memory
# Startzeit der Firewall
# Uptime of the firewall
system diagnostics show uptime
# Versionen von SFOS, Modulen, Signaturen
# Versions of SFOS, modules, signatures
system diagnostics show version-infoRouting / SD WAN
System-generated and response traffic
If you want to control how the firewall routes system traffic or response packets, you can do this using SD-WAN rules. However, it is important that the option is switched on in each case. In older firewalls or configuration versions, the option is still deactivated. With any release, the options are activated from the start.
The status of the configuration can be checked in the WebUI.
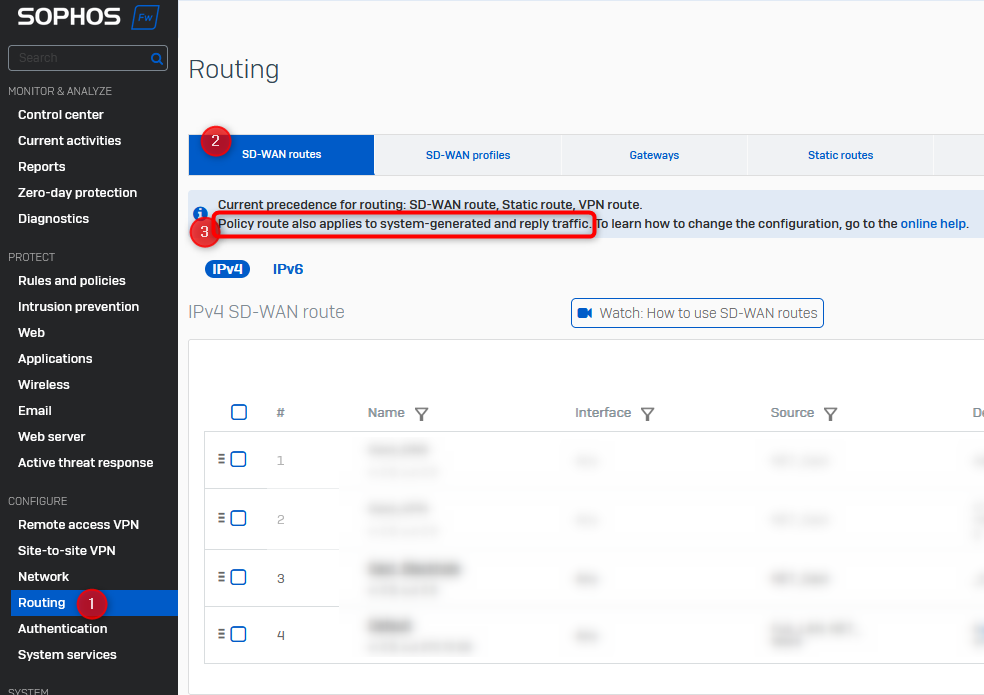
The setting can only be changed via the console.
# Aktuelle Konfiguration anzeigen
# Check status for reply or systemgenerated pakets
show routing sd-wan-policy-route reply-packet
show routing sd-wan-policy-route system-generate-traffic
# Konfiguration ändert
# Change status
set routing sd-wan-policy-route [system-generate-traffic | reply-packet] [enable | disable]Routing priority
Depending on the routing structure, the order of the routing paths in the firewall can be important.
For example, there are two routes to a target network - VPN and MPLS (static route). Either the VPN route should be preferred and the MPLS route is a backup, or the other way around. In this case, the priority in the firewall must be adjusted.
The status of the configuration can be checked in the WebUI.
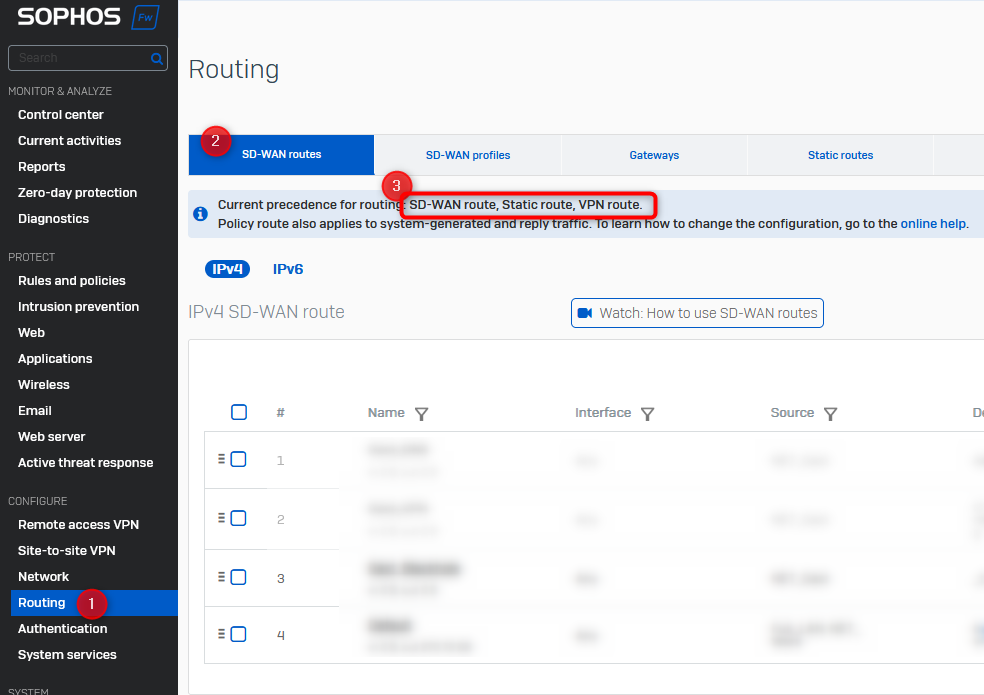
The setting can only be changed via the console.
# Aktuellen Status anzeigen
# Show current precedence
system route_precedence show
# Reihenfolge ändern (Reihenfolge beliebig setzen: vpn static sdwan_policyroute)
# Change precedence (set precedence to you own order: vpn static sdwan_policyroute)
system route_precedence set vpn static sdwan_policyroute
system route_precedence set static vpn sdwan_policyroute
# usw. / and so onCheck route / clear cache
There is also an option in the console to check a route used for an IP address. In other words, which gateway is being used.
system diagnostics utilities route lookup 172.16.16.16To clear the current routing cache and force the firewall to re-read the routes:
system diagnostics utilities route flush-cacheIPS Settings
Full / reduced package
The Sophos Firewall can use a full or a reduced IPS signature package. The full package is of course much more comprehensive, but requires more memory
# Status anzeigen
# Show status
system ips full-signature-pack show
# Zwischen den Paketen wechseln
# Switch between full and reduced pack
system ips full-signature-pack [ enable | disable ]Increase detection rate
Sophos does not use all data packets in a data stream for IPS detection. This has performance reasons and is therefore set to only the first 8 packets. However, it can also lead to incorrect detections or that no signature takes effect at first. However, the behavior can be adjusted and even extended to the entire data stream.
# Status anzeigen
# Show status
show ips-settings
# Anzahl der Pakete verändern
# Change number of pakets
set ips maxpkts [<number> | all | default = 8]Application Control
Application classification and ATP exceptions
The application classification of individual rules can be deactivated. However, ATP is then also excluded for this rule. This may be necessary in some cases, as the WebUI does not offer these options.
# Einstellungen anzeigen
# Show current settings
show ips-settings
# Ausnahme setzen
# Set exceptions
set ips ac_atp exception fwrules <rule IDs, comma separated># Einstellungen anzeigen
# Show current settings
show ips-settings
# Ausnahme setzen
# Set exceptions
set ips ac_atr exception fwrules <rule IDs, comma separated>Microapp detection
The detection of microapps can also only be activated or deactivated globally via the console. As far as I know, this is not activated by default. Please also note that the detection runs via IPS and a higher number of packets may be required for detection if the apps are not detected properly. See here. It also requires more system resources.
# Status anzeigen
# Show status
system application_classification microapp-discovery show
# Klassifizierung umstellen
# Set application classification
system application_classification microapp-discovery [on | off]Captchas
The captchas on the login screens can be deactivated for the WebAdmin and user portal.
system captcha-authentication-global [show | disable | enable] disable for webadminconsolesystem captcha-authentication-global [show | disable | enable] for userportalSeparately, this can also only be configured for the VPN zone.
system captcha-authentication-vpn [show | disable | enable] for webadminconsole
system captcha-authentication-vpn [show | disable | enable] for userportalModules
In the Sophos firewall, modules that process data packets run hidden in the background. These include a SIP and H323 proxy, which I would now like to discuss. A SIP proxy on the Sophos Firewall serves as an intermediary for VoIP communication by receiving SIP requests and forwarding them to the appropriate destinations. It performs tasks such as call forwarding, authentication, authorization and security measures to ensure efficient and secure voice communication over IP networks. However, this often leads to connection errors in Germany. If this is the case, the modules must be deactivated. The configuration is of course boot-resistant.
# Status anzeigen
# Show status of modules
system system_modules show
# Module deaktivieren
# Unload modules or load again.
system system_modules sip [ unload | load ]
system system_modules h323 [ unload | load ]The other modules TFTP, IRC, DNS and PPTP can be deactivated in the same way.
User portal link
A link to the user portal is displayed in the VPN portal by default. This can be hidden here.
system userportal-linkon-vpnportal [disable | enable | show ]ARP
The ARP table of the firewall can be displayed here:
# ARP komplett anzeigen
# Show all ARP
system diagnostics utilities arp show
# Spezifischen Antrag anzeigen
# Show ARP for IP addresss or interface
system diagnostics utilities arp show [<IP> | interface]Statistics
Display of the number of all active connections.
system diagnostics utilities connections countDisplay of details for all connections, or for selected ones
# Anzeigen für alle Verbindungen
# Show details for all connections
system diagnostics utilities connections v4 show
# Anzeigen für eine spezielle Verbindung
# show details for selected connections
system diagnostics utilities connections v4 show [ src_ip s.s.s.s | dest_ip d.d.d.d | proto tcp/udp/icmp ]


