
In this article we present some Sophos Firewall CLI commands – for the console and the advanced shell. Feel free to browse through. Maybe you’ll find something new! 😊
Introduction
The following Sophos Firewall CLI commands for the Advanced Shell and Console are all tested with versions 19.x.x. However, they should work in the same way in version 20+. I will gradually expand the overview.
We accept no liability for problems or damage that may arise from the use of the commands listed here!
In general, the shell and console should only be used by experienced persons. If in doubt, please contact your Sophos partner.
Firewall Console
Check hotfix status
The hotfix status cannot be checked in the WebUI. If you want to check your current hotfix status on the console, enter the following here:
system diagnostic show version-infoIP countries review
You want to have the country associated with a certain IP address in order to optimize the rules accordingly? The Console offers an option for this:
show country-host ip2country ipaddress 8.8.8.8Advanced Shell
tcpdump
We have written a separate article for tcpdump. Have a look here: Sophos Firewall Cookbook: tcpdump
conntrack with readable time stamp
Unfortunately, conntrack does not offer the possibility to display the timestamps in a readable format. However, this can still be solved with a pipe command.
- from “-o …” is required for the readable timestamp
- You can continue to set the parameters in front of it (here -E) according to your requirements
conntrack -E -o timestamp | awk -F "[\t]" '{ gsub(/(\[)/,"",$1) ;gsub(/(\])/,"",$1); print strftime("%c",$1) " " $2 }'conntrack – Parameters and fields
The conntrack tool is very useful for checking open or new connections of the Sophos Firewall. A small documentation on conntrack can be found in an article from Sophos: Sophos Firewall: CLI Troubleshooting Tools
Test SSL connection
You want to test whether the Sophos Firewall itself can establish an SSL connection, or whether the certificate is correct for the connection? The solution is openssl.
openssl s_client -connect sophos.com:443Show detected SFP transceivers
You wanted to know if and which transceiver the Sophos Firewall has recognized in an SFP/SFP+ port. It works with “ethtool”.
ethtool -m PortF1Quick change to the console
Everyone will be familiar with this. If you have to jump back and forth between the Advanced Console and the Console frequently, it often becomes annoying. I therefore always recommend going directly to the Advanced Shell. There are two commands here with which you can quickly switch to the console! Exit then takes you back to the Advanced Shell. Super practical! 😊
cishcshCSC Service Debug
The CSC service cannot be set to debug with the familiar “service” command. There is a separate command here. To deactivate, simply enter the command again
csc custom debugCheck whether debug has been set or deactivated:
cat /log/csc.log | grep Toggling | tail -n 10AKTIVIERT:
MESSAGE Oct 31 10:00:26Z [worker:11599]: Toggling log level to: MAX
DEAKTIVIERT
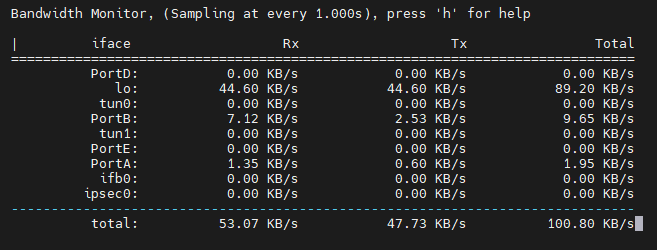
MESSAGE Oct 31 10:04:20Z [worker:23646]: Toggling log level to: WARNINGbwmon – Interface Bandwidth Monitor
With “bwmon”, the current load per interface can be displayed in the shell.
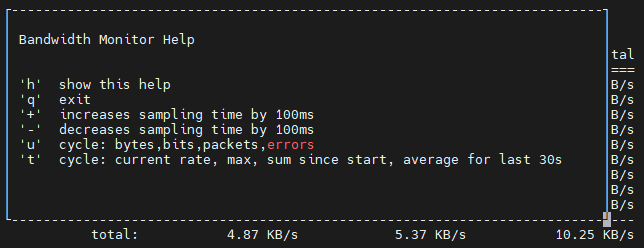
bwmonOnce started, the current load is displayed at 0.5 second intervals. If you press “h” you will get a little help. This explains how to adjust the sampling intervals or the display of the throughput.
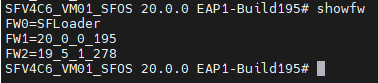
showfw – Show versions in firmware slots
showfw displays the firmware versions in the two firmware slots.
Show webadmin port
You have shell access, but don’t know which port the web interface is running on? The configured ports can be found out with a database query.
psql -U nobody -d corporate -c "select destinationport from tbllocalservicedetails WHERE localserviceid =2"

Danke, für die Auflistung. Sind ein paar neue Sachen bei für mich. Gibt es eine zweiten Teil?
Hallo Manfred,
Freut mich. Ja, der zweite ist in Arbeit. Das wird aber noch ein paar Wochen dauern. Schau einfach regelmäßig vorbei. 😊
Gruß,
Sebastian
Great info, looking forward to part 2, hopefully with opcode. 🙂 Also, drppkt is a very useful tool, which could be mentioned either here or in the tcpdump article.
Thank you for your feedback. I am currently working on 2-3 articles for the CLI which will also replace the old one. I hope to be ready in November. opcode would also be very cool, but unfortunately Sophos itself is very secretive about it and you only get a little information here. But I am already collecting 😉